CyberKey smart keys are designed with highly durable…
CyberKey smart keys are designed with highly durable fiberglass-reinforced casings and are programmed with access permissions for each key holder.
CyberKey smart keys are designed with highly durable…
CyberKey smart keys are designed with highly durable fiberglass-reinforced casings and are programmed with access permissions for each key holder.
CyberKey smart keys are designed with highly durable…
CyberKey smart keys are designed with highly durable fiberglass-reinforced casings and are programmed with access permissions for each key holder.
CyberLock was first to market with Bluetooth key…
CyberLock was first to market with Bluetooth key technology 7 years ago. CyberKey Blue 2, our latest dual-mode Bluetooth key, extends battery life, requiring only one charge per week!
The CK-Air2 is an advances game-changing electronic key…
The CK-Air2 is an advances game-changing electronic key used to operate CyberLock cylinders and FlashLock access points. The addition of a feedback screen and the FlashLock wireless ability sets it apart from CK-Air (which is also available).
The CyberKey X combines the increased memory capacity…
The CyberKey X combines the increased memory capacity of Generation 2 CyberKeys with the infrared technology and replaceable battery of Generation 1 CyberKeys. The memory can hold up to 12,000 locks or audit events, or up to 100 lock downloads. It also has enhanced abilities in terms of delayed activation and temporary access.
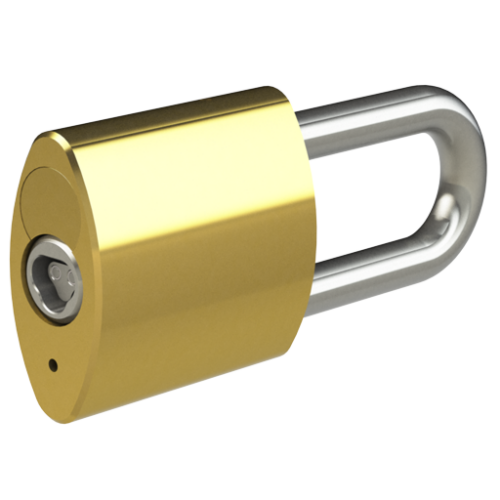
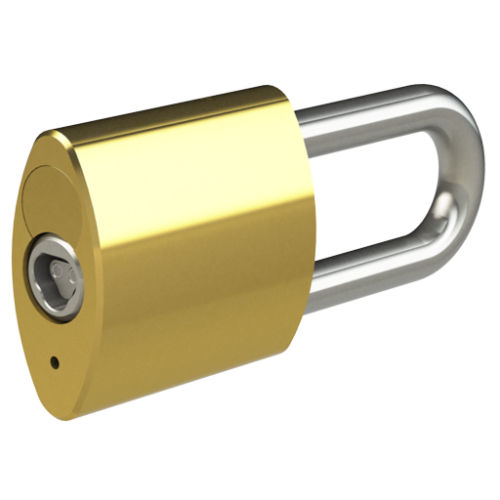
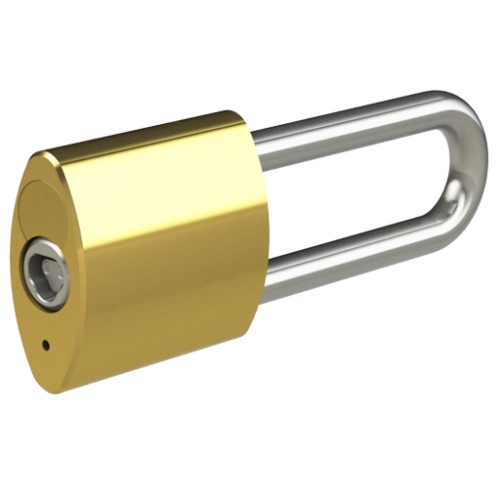
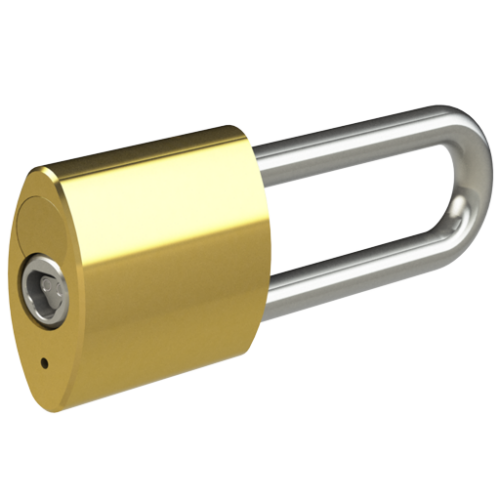
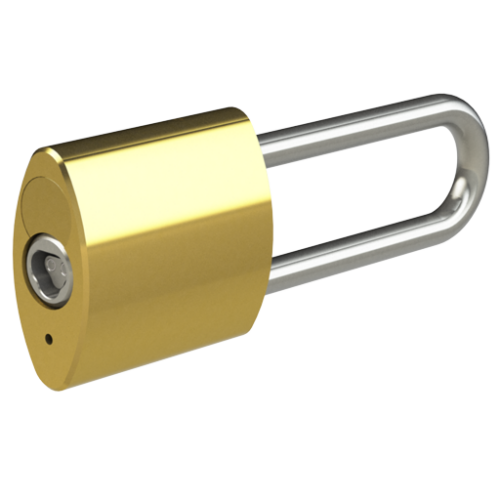
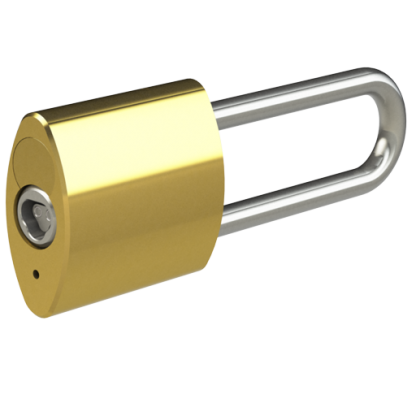
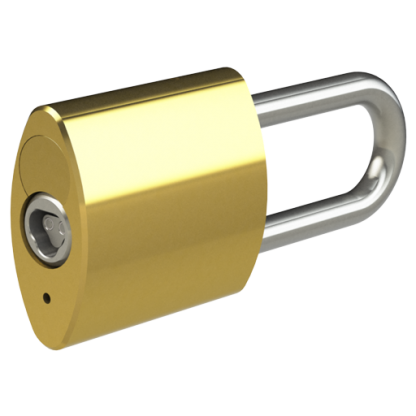
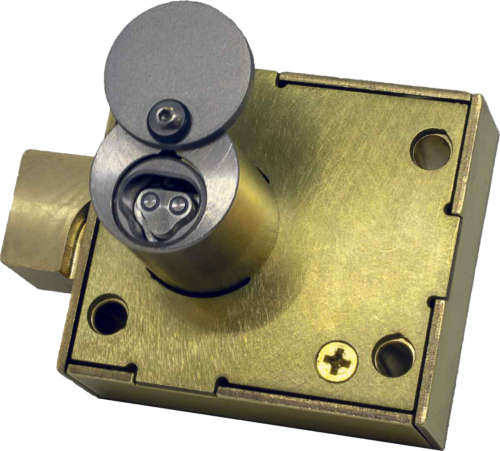
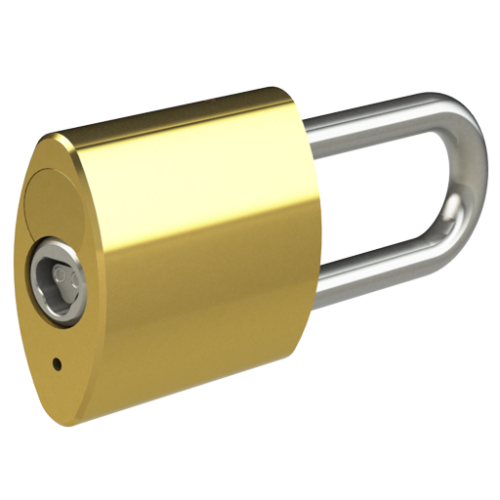
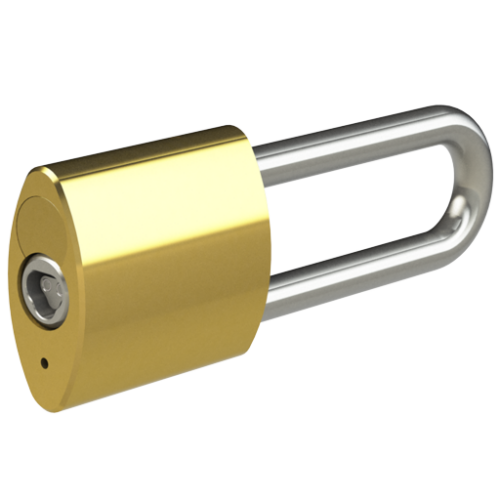
We offer a wide range of Padlock styles…
We offer a wide range of Padlock styles and strengths, including Open and Closed shackle designs, Brass and Stainless Steel varieties, and also CEN Level 4, 5 and 6 Security accredited Padlocks for highly challenging environments. The Hockey Puck Padlock has no visible shackle – and the Trailer Lock provides mobile asset security.
Over 400 different CyberLock designs are available! However,…
Over 400 different CyberLock designs are available! However, we also recognise that your challenge might be unique and therefore we will try and accomodate your need. We are enthusiastic about the challenge.
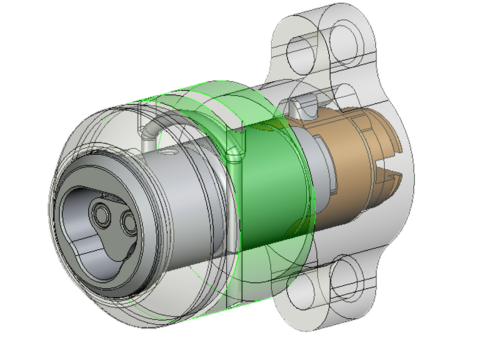
Controlled access using CyberLock is powerful and flexible…
Controlled access using CyberLock is powerful and flexible -but there are circumstances where the issue of a Key (whether mechanical or electronic) is simply impractical. Should every delivery driver to your premises have a Key or an access code? What about the countless engineers that might need to visit your remote sites occasionally? Or even the holiday-makers who need access to your Apartment for two weeks in the year?
The IR Encoder 10 is a small and…
The IR Encoder 10 is a small and portable infrared device that connects to a USB port of a Windows Computer, and it works with CyberLink software to update CyberKeys that are IR enabled. Launch the software and simply line up the key infrared port and IR Encoder 10 infrared port to begin the communication process.
The CKS-020 is a highly rugged and versatile…
The CKS-020 is a highly rugged and versatile means of configuring, updating and charging CyberKeys. It works equally well with the older CyberLink software and the newer, faster CyberLink 2.
Introducing the ValidiKey 20 Cabinet solution, which features…
Introducing the ValidiKey 20 Cabinet solution, which features both LAN and WiFi connections, making it flexible to deploy. It also features an integrated touch screen, so that entry of PIN and Job Codes is achieved easily. The screen also provides User feedback on the collection and return of CyberKeys. This cabinet if fully compatible with the generation 2 CyberKey range – as well as Generation 1 rechargeable CyberKeys (CK-RXD and CK-RXD2).
CyberLock communication devices serve as the interface between…
CyberLock communication devices serve as the interface between CyberLock hardware and CyberAudit management software. Access privileges are distributed to key holders via communicators. These devices are linked to the software over a local area network or securely over the Internet. When a CyberKey and communicator make contact, the audit trail is downloaded from the key while simultaneously new schedules, permissions, and system information are uploaded to the key. To increase security and accountability, access privileges can be programmed to expire at scheduled intervals. This results in users regularly updating and reauthorizing keys at communicators.
The is a highly versatile Keypad with the…
The is a highly versatile Keypad with the facility to update CyberKeys, but also check they are being used by the correct person (with PIN cotrol activated where this is essential). In addition, the AK-01 allows shared Keys to be activated with a Job Number, making it ideal for contractor control.
CyberLock communication devices serve as the interface between…
CyberLock communication devices serve as the interface between CyberLock hardware and CyberAudit management software. Access privileges are distributed to key holders via communicators. These devices are linked to the software over a local area network or securely over the Internet. When a CyberKey and communicator make contact, the audit trail is downloaded from the key while simultaneously new schedules, permissions, and system information are uploaded to the key. To increase security and accountability, access privileges can be programmed to expire at scheduled intervals. This results in users regularly updating and reauthorizing keys at communicators.
The CKV-020S holds up to 20 Generation 1…
The CKV-020S holds up to 20 Generation 1 CyberKeys. It allows the addition of your own screen using a standard HDMI cable. Entry of PIN and Job Codes is achieved easily using the integrated KeyPad. This cabinet if fully compatible with the generation 1 CyberKey range – (CK-RXD and CK-RXD2).
The Flex weatherized external vault is special. It…
The Flex weatherized external vault is special. It allows inert CyberKeys to be located at remote sites, fully charged and ready to be activated by an authorised user with a valid Job code (and PIN if desired). The date of obtaining the Key using these codes can be restricted by date range and times. The time of collection and return of the Key may be monitored in real-time. The Vault in not only highly attack resistant – but the Key inside has no intrinsic security value since it will not work until properly authorised.
CyberLock is controlled using flexible software that streamlines…
CyberLock is controlled using flexible software that streamlines business processes, cutting costs and creating efficiencies through problem solving capability. It provides ease online connection to locks, keys and the entire suite of communication devices including key cabinets, safes and mobile Apps. CyberAuditWeb is the authorised software for management of CyberLock systems of all sizes. CyberAuditWeb allows you to assign keys, set expirations, add new lock cylinders, monitor activity of staff and contractors, create access schedules, and generate audit trails & custom reports.
The CyberKey Blue3 is the most advanced CyberKey.…
The CyberKey Blue3 is the most advanced CyberKey. It is a powerful and flexible Generation 2 Key designed for mobile workforces.
Brass, 1” x 3/8” diameter stainless steel shackle
Brass, 1” x 3/8” diameter stainless steel shackle
Brass, 1” x 3/8” diameter stainless steel shackle,…
Brass, 1” x 3/8” diameter stainless steel shackle, key retaining
Brass, 2” x 3/8” diameter stainless steel shackle
Brass, 2” x 3/8” diameter stainless steel shackle
Brass, 2” x 3/8” diameter stainless steel shackle,…
Brass, 2” x 3/8” diameter stainless steel shackle, key retaining
Brass, 3” x 3/8” diameter stainless steel shackle
Brass, 3” x 3/8” diameter stainless steel shackle
Brass, 3” x 3/8” diameter stainless steel shackle,…
Brass, 3” x 3/8” diameter stainless steel shackle, key retaining
Stainless Finish, 25mm 8mm shackle, key retaining, CEN…
Stainless Finish, 25mm 8mm shackle, key retaining, CEN 1, KIK Cylinder
Stainless Finish, 60mm 8mm shackle, key retaining, CEN…
Stainless Finish, 60mm 8mm shackle, key retaining, CEN 1, KIK Cylinder
Stainless Finish, 110mm 8mm shackle, key retaining, CEN…
Stainless Finish, 110mm 8mm shackle, key retaining, CEN 1, KIK Cylinder
Stainless Finish, 25mm 8mm shackle, key retaining, CEN…
Stainless Finish, 25mm 8mm shackle, key retaining, CEN 2, OVL Cylinder
Stainless Finish, 25mm 8mm shackle, key retaining, CEN…
Stainless Finish, 25mm 8mm shackle, key retaining, CEN 2, OVLWR Cylinder
Stainless Finish, 60mm 8mm shackle, key retaining, CEN…
Stainless Finish, 60mm 8mm shackle, key retaining, CEN 2, OVL Cylinder
Stainless Finish, 60mm 8mm shackle, key retaining, CEN…
Stainless Finish, 60mm 8mm shackle, key retaining, CEN 2, OVLWR Cylinder
Stainless Finish, 110mm 8mm shackle, key retaining, CEN…
Stainless Finish, 110mm 8mm shackle, key retaining, CEN 2, OVL Cylinder
Stainless Finish, 110mm 8mm shackle, key retaining, CEN…
Stainless Finish, 110mm 8mm shackle, key retaining, CEN 2, OVLWR Cylinder
Stainless Finish, 28mm 11mm shackle, key retaining, CEN…
Stainless Finish, 28mm 11mm shackle, key retaining, CEN 3, OVL Cylinder
Stainless Finish, 28mm 11mm Protected shackle, key retaining,…
Stainless Finish, 28mm 11mm Protected shackle, key retaining, CEN 3, OVL Cylinder