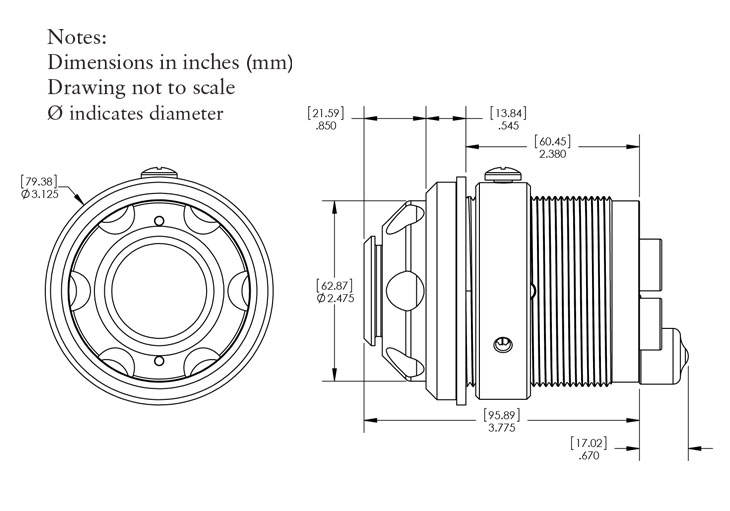
The Flex weatherized external vault is special. It allows inert CyberKeys to be located at remote sites, fully charged and ready to be activated by an authorised user with a valid Job code (and PIN if desired). The date of obtaining the Key using these codes can be restricted by date range and times. The time of collection and return of the Key may be monitored in real-time. The Vault in not only highly attack resistant – but the Key inside has no intrinsic security value since it will not work until properly authorised.
FS-CV01
Vending CyberKeys at Remote Locations
Key control is traditionally managed from a central location such as a security office or reception area, close to an operation of work. Staff and contractors might sign keys out and then bring them back after use. Typically this can involve manual paper records logging who took what keys and when. Administration can be costly and the process is inefficient. For remote workers this may require excessive travel time.
There is a better way. Flex Vaults secure CyberKeys in the location where they are needed whilst being under the total control of the system administrator. The Vaults can be installed outdoors and in harsh environments. Each Vault retains one unprogrammed, deactivated key. The key is programmed and activated when the keyholder presents their credentials by RFID card or PIN code.
The keyholder must have permission to remove the key at a pre-determined time and date. When the key is removed it is electronically assigned to the keyholder and carries their unique access privileges, such as what locks it can open and when. The key can be set to expire, so if it is not returned on time it will deactivate. Flex Vaults also send real-time information to the system administrator, detailing who has taken the key and when. Reports also include the keys audit trail information.